For the Cisco CCNA 200-301 exam, the most deserving are valid CCNA 200-301 preparation resources. It will take you through the exam with ease. Well, I think you’ll need the latest version of the 200-301 exam dumps to provide you with the latest CCNA 200-301 preparation resources.
200-301 exam dumps new download address: https://www.pass4itsure.com/200-301.html contains 825 exam questions and answers to help test takers pass the exam.
Do you really know about the Cisco CCNA 200-301 exam?

In the real 200-301 exam you need to answer about 100-120 questions in 120 minutes, and the exam costs $300.
Knowing the basic knowledge points is not enough to pass the Cisco CCNA 200-301 exam. Be aware that passing the exam also requires help with a valid CCNA 200-301 preparation resource.
How to effectively prepare for the Implementing and Administering Cisco Solutions exam?
After knowing the basic points of the exam, you will enter the most critical step, how to prepare for the 200-301 exam.
I think you need help with the Pass4itSure 200-301 exam dumps. It will provide you with effective CCNA 200-301 preparation resources to help you overcome the exam.
After getting dumps, you should do this:
Start by regularly reviewing the basic content concepts of the 200-301 exam and practicing the exam questions regularly. Then, review your confusion while doing the question and ask experts and experienced IT professionals for help.
Where can I get free 200-301 exam questions new by professionals?
Examproof.com prepare free 200-301 questions for you.
You can download the Cisco 200-301 questions PDF below: https://drive.google.com/file/d/1_cRoAyec2CHnwI5mExIJHV6REAbNOEyR/view?usp=sharing
Perhaps, you also want to read the free online 200-301 exam questions:
Q-1.
Which set of actions satisfy the requirement for multifactor authentication?
A. The user enters a username and password and then re-enters the credentials on a second screen.
B. The user swipes a key fob, then clicks through an email link.
C. The user enters a username and password and then clicks a notification in an authentication app on a mobile device.
D. The user enters a PIN into an RSA token, and then enters the displayed RSA key on a login screen.
Correct Answer: C
This is an example of how two-factor authentication (2FA) works:
1. The user logs in to the website or service with their username and password.
2. The password is validated by an authentication server and, if correct, the user becomes eligible for the second factor.
3. The authentication server sends a unique code to the user\\’s second-factor method (such as a smartphone app).
4. The user confirms their identity by providing additional authentication for their second-factor method.
Q-2.
Refer to the exhibit. Site A was recently connected to site B over a new single-mode fiber path. Users at site A report Intermittent connectivity Issues with applications hosted at site B. What is the reason for the problem?

A. Heavy usage is causing high latency.
B. An incorrect type of transceiver has been inserted into a device on the link.
C. physical network errors are being transmitted between the two sites.
D. The wrong cable type was used to make the connection.
Correct Answer: C
Q-3.
What benefit does controller-based networking provide versus traditional networking?
A. allows configuration and monitoring of the network from one centralized port
B. provides an added layer of security to protect from DDoS attacks
C. combines control and data plane functionality on a single device to minimize latency
D. moves from a two-tier to three-tier network architecture to provide maximum redundancy
Correct Answer: A
Q-4.
Refer to the exhibit.
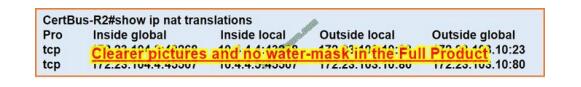
An engineer configured NAT translations and verified that the configuration is correct. Which IP address is the source IP?
A. 10.4.4.4
B. 10.4.4.5
C. 172.23.103.10
D. 172.23.104.4
Correct Answer: D
The packet starts off with address 10.4.4.5 (Inside Local). It gets translated to 172.23.104.4 (Inside Global).
It\\’s destination is 172.23.103.10 (Outside Global). It may get matted at the destination, but to the source NAT Engine it is still 172.23.103.10.
Q-5.
Refer to the exhibit. Which route must be configured on R1 so that OSPF routing is used when OSPF is up? but the server is still reachable when OSPF goes down?
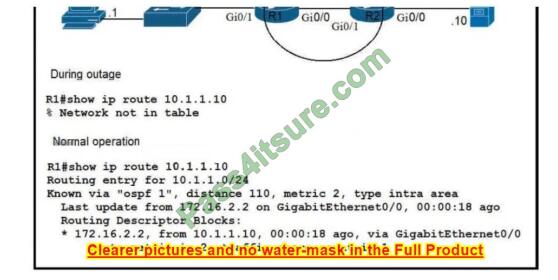
A. ip route 10.1.1.10 255.255.255.255 172.16.2.2 100
B. ip route 10.1.1.0 255.255.255.0 gi0/1 125
C. ip route 10.1.1.0 255.255.255.0 172.16.2.2 100
D. ip route 10.1.1.10 255.255.255.255 gi0/0 125
Correct Answer: D
Q-6.
Refer to the exhibit.
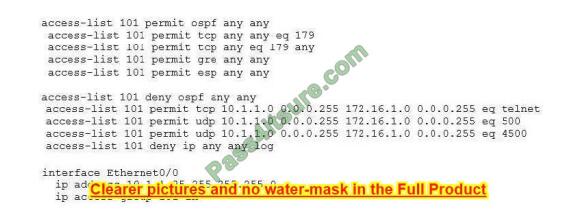
A network administrator has been tasked with securing VTY access to a router Which access-list entry accomplishes this task?
A. access-list 101 permit TCP 10.1.10 0.0.0.255 172.16.10 0.0.0.255 eq ssh
B. access-list 101 permit TCP 10.11.0 0.0.0.255 172.16.10 0.0.0.255 eq SCP
C. access-list 101 permit tcp 10.11.0 0.0.0.255 172.16.10 0.0.0.255 eq telnet
D. access-list 101 permit TCP 10.1.10 0.0.0.255 172.16.10 0.0.0.255 eq HTTPS
Correct Answer: A
Q-7.
When a site-to-site VPN is used, which protocol is responsible for the transport of user data?
A. IPsec
B. IKEv1
C. MD5
D. IKEv2
Correct Answer: A
A site-to-site VPN allows offices in multiple fixed locations to establish secure connections with each other over a public network such as the Internet. A site-to-site VPN means that two sites create a VPN tunnel by encrypting and sending data between two devices. One set of rules for creating a site-to-site VPN is defined by IPsec.
Q-8.
What is the binary pattern of unique ipv6 unique local address?
A. 00000000
B. 11111100
C. 11111111
D. 11111101
Correct Answer: B
An IPv6 Unique Local Address is an IPv6 address in the block FC00::/7, which means that IPv6 Unique Local addresses begin with 7 bits with the exact binary pattern as 1111 110 -> Answer B is correct. Note: IPv6 Unique Local Address is the approximate IPv6 counterpart of the IPv4 private address. It is not routable on the global Internet.
Q-9.
Which device tracks the state of active connections in order to make a decision to forward a packet through?
A. wireless access point
B. firewall
C. wireless LAN controller
D. router
Correct Answer: C
Q-10.
Which mode must be used to configure EtherChannel between two switches without using a negotiation protocol?
A. active
B. on
C. auto
D. desirable
Correct Answer: B
The Static Persistence (or “on” mode) bundles the links unconditionally and no negotiation protocol is used. In this mode, neither PAgP nor LACP packets are sent or received.
Q-11.
A network administrator is asked to configure VLANs 2, 3, and 4 for a new implementation. Some ports must be assigned to the new VLANS with unused remaining. Which action should be taken for the unused ports?
A. configure the port in the native VLAN
B. configure ports in a black hole VLAN
C. configure in a non-default native VLAN
D. configure ports as access ports
Correct Answer: B
Q-12.
Which command is used to enable LLDP globally on a Cisco IOS ISR?’
A. lldp run
B. lldp enable
C. lldp transmit
D. cdp run
E. cdp enable
Correct Answer: A
Link Layer Discovery Protocol (LLDP) is an industry-standard protocol that allows devices to advertise, and discover connected devices, and their capabilities (same as the CDP of Cisco). To enable it on Cisco devices, we have to use this command under global configuration mode: Sw(config)# lldp run
Q-13.
What is the purpose of an SSID?
A. It provides network security
B. It differentiates traffic entering access posts
C. It identifies an individual access point on a WLAN
D. It identifies a WLAN
Correct Answer: D
In IEEE 802.11 wireless local area networking standards (including Wi-Fi), a service set is a group of wireless network devices that share a service set identifier (SSID) … A service set forms a logical network of nodes operating with shared link-layer networking parameters; they form one logical network segment.
On this blog, not only do you have answers to questions about the Cisco 200-301 exam, but also get the latest 200-301 dumps practice questions, and for more Cisco 200-301 exam questions, download the latest version of the 200-301 exam dumps: https://www.pass4itsure.com/200-301.html