As the gold standard in cybersecurity, the CISSP (Certified Information Systems Security Professional) certification, issued by (ISC)² Official Site, remains unrivaled in 2025. According to the (ISC)² 2024 Report, global CISSP holders saw an average salary increase of 12%, underscoring its career value.
This article will analyze the new changes in the 2025 CISSP exam, uncover prep pitfalls, and share practical strategies to help you pass smoothly. I’m Carmen Lee, a CISSP holder with 10 years of training experience, hoping this serves as your exam “navigator.”
What’s Next for the CISSP Exam in 2025
According to the (ISC)² Exam Outline(updated April 15, 2024), the CISSP 8 domains’ weights were adjusted in 2024 and remain the basis for the 2025 exam. For instance, Domain 1 (Security and Risk Management) increased from 15% to 16%, while Domain 8 (Software Development Security) dropped from 11% to 10%. As of March 2025, no new weight changes have been announced by (ISC)², but candidates should focus on:
- Domain 3: Security Architecture and Engineering: Cloud security and zero trust remain key topics.
- Domain 5: Identity and Access Management: MFA and biometric questions are prominent.
- Domain 7: Security Operations: Incident response and threat hunting case studies stay critical.
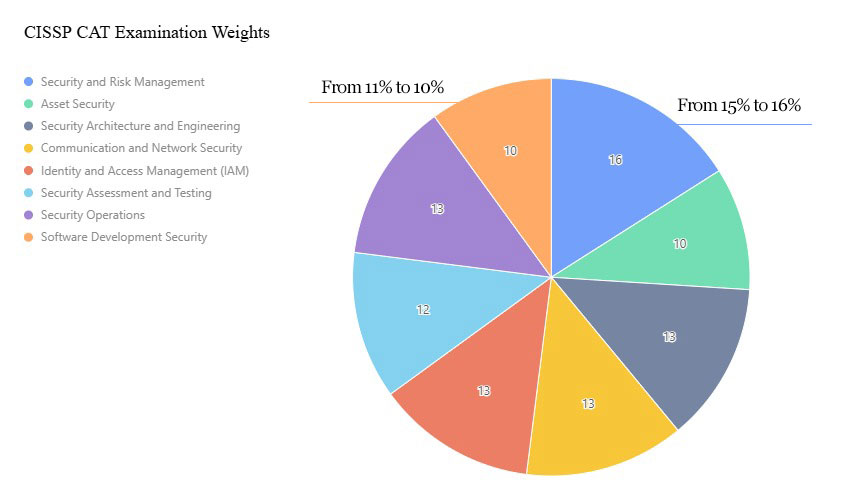
Candidates in 2025 should emphasize practical skills aligned with current industry needs.
Impact of AI and Emerging Technologies
Artificial Intelligence (AI) and Machine Learning (ML) are deeply impacting cybersecurity. Per SANS Research, AI-related questions made up 15% of the 2024 CISSP exam, such as “How to use AI to detect anomalous traffic.” This trend may persist in 2025, requiring candidates to understand AI applications in security and managerial evaluation.
Additionally, quantum computing and 5G may appear in encryption questions. Refer to the NIST Cybersecurity Framework to bolster technical knowledge.
Hidden Pitfalls: Common CISSP 2025 Prep Mistakes
Pitfall 1: Relying on Outdated Materials
Since the 2024 CAT mode update (3 hours, 100-150 questions), old question banks are outdated.
Solution: Use synced resources like Pass4itsure Latest Dumps, covering 2025 question types.
Pitfall 2: Neglecting Time Management
In CAT mode, spending over 1 hour on the first 50 questions spikes later difficulty.
Solution: Keep each question within 1-1.5 minutes with ample practice.
Pitfall 3: Over-Reliance on Technical Thinking
CISSP favors managerial decisions, e.g., “Prioritize disaster recovery during outages,” not tech details.
Solution: Train managerial thinking with scenario questions.
Online Sharing: Latest 2025 CISSP Questions
Here are some examples of real exam questions based on the 2025 trends:
| Free share | Contrast |
| 15 Q&As | 2024 Cissp Questions |
1. Which of the following could cause a Denial of Service (DoS) against an authentication system?
A. Encryption of audit logs
B. No archiving of audit logs
C. Hashing of audit logs
D. Remote access audit logs
Correct Answer: B
2. What is the second phase of Public Key Infrastructure (PKI) key/certificate life-cycle management?
A. Implementation Phase
B. Initialization Phase
C. Cancellation Phase
D. Issued Phase
Correct Answer: D
3. Which type of disaster recovery plan (DRP) testing carries the MOST operational risk?
A. Cutover
B. Walkthrough
C. Tabletop
D. Parallel
Correct Answer: C
4. Directive controls are a form of change management policy and procedures. Which of the following subsections are recommended as part of the change management process?
A. Build and test
B. Implement security controls
C. Categorize Information System (IS)
D. Select security controls
Correct Answer: A
5. A Security Operations Center (SOC) receives an incident response notification on a server with an active intruder who has planted a backdoor. Initial notifications are sent and communications are established.
What MUST be considered or evaluated before performing the next step?
A. Notifying law enforcement is crucial before hashing the contents of the server hard drive
B. Identifying who executed the incident is more important than how the incident happened
C. Removing the server from the network may prevent catching the intruder
D. Copying the contents of the hard drive to another storage device may damage the evidence
Correct Answer: C
6. When designing a new Voice over Internet Protocol (VoIP) network, an organization\’s top concern is preventing unauthorized users accessing the VoIP network. Which of the following will BEST help secure the VoIP network?
A. Transport Layer Security (TLS)
B. 802.1x
C. 802.119
D. Web application firewall (WAF)
Correct Answer: A
7. Which of the following is part of a Trusted Platform Module (TPM)?
A. A non-volatile tamper-resistant storage for storing both data and signing keys in a secure fashion
B. A protected Pre-Basic Input/Output System (BIOS) which specifies a method or a metric for “measuring” the state of a computing platform
C. A secure processor targeted at managing digital keys and accelerating digital signing
D. A platform-independent software interface for accessing computer functions
Correct Answer: A
8. What Hypertext Transfer Protocol (HTTP) response header can be used to disable the execution of inline JavaScript and the execution of eval()-type functions?
A. Strict-Transport-Security
B. X-XSS-Protection
C. X-Frame-Options
D. Content-Security-Policy
Correct Answer: D
9. A breach investigation …… a website was exploited through an open soured …..Is The FIRB Stan In the Process that could have prevented this breach?
A. Application whitelisting
B. Web application firewall (WAF)
C. Vulnerability remediation
D. Software inventory
Correct Answer: B
10. When a system changes significantly, who is PRIMARILY responsible for assessing the security impact?
A. Chief Information Security Officer (CISO)
B. Information System Owner
C. Information System Security Officer (ISSO)
D. Authorizing Official
Correct Answer: B
11. Refer to the information below to answer the question.
During the investigation of a security incident, it is determined that an unauthorized individual accessed a system which hosts a database containing financial information. Aside from the potential records which may have been viewed, which of the following should be the PRIMARY concern regarding the database information?
A. Unauthorized database changes
B. Integrity of security logs
C. Availability of the database
D. Confidentiality of the incident
Correct Answer: A
12. Which of the following BEST describes why software assurance is critical in helping prevent an increase in business and mission risk for an organization?
A. Software that does not perform as intended may be exploitable which makes it vulnerable to attack.
B. Request for proposals (RFP) avoid purchasing software that does not meet business needs.
C. Contracting processes eliminate liability for security vulnerabilities for the purchaser.
D. Decommissioning of old software reduces long-term costs related to technical debt.
Correct Answer: A
13. An organization is implementing data encryption using symmetric ciphers and the Chief Information Officer (CIO) is concerned about the risk of using one key to protect all sensitive data. The security practitioner has been tasked with recommending a solution to address the CIO\’s concerns. Which of the following is the BEST approach to achieving the objective by encrypting all sensitive data?
A. Use a Secure Hash Algorithm 256 (SHA-256).
B. Use Rivest-Shamir-Adleman (RSA) keys.
C. Use a hierarchy of encryption keys.
D. Use Hash Message Authentication Code (HMAC) keys.
Correct Answer: B
14. As a security manger which of the following is the MOST effective practice for providing value to an organization?
A. Assess business risk and apply security resources accordingly
B. Coordinate security implementations with internal audit
C. Achieve compliance regardless of related technical issues
D. Identify confidential information and protect it
Correct Answer: D
15. What is the MOST effective way to ensure that a cloud service provider does not access a customer\’s data stored within its infrastructure?
A. Use the organization\’s encryption tools and data management controls.
B. Ensure that the cloud service provider will contractually not access data unless given explicit authority.
C. Request audit logs on a regular basis.
D. Utilize the cloud provider\’s key management and elastic hardware security module (HSM) support.
Correct Answer: B
Reference: https://uncitral.un.org/sites/uncitral.un.org/files/media-documents/uncitral/en/19-09103_eng.pdf
Expert Tips: Efficient 2025 CISSP Success Strategies
- Phased Learning: Tackle 1-2 domains weekly, focusing on weaknesses.
- Quality Resources: Pair official materials with Pass4itsure Practice Tools for real-world readiness.
- Mock Exams: Run 1-2 full simulations weekly to master CAT pacing.
- Community Interaction: Join (ISC)² Forumto exchange insights.
Conclusion: Your Path to CISSP Success
The 2025 CISSP exam offers big opportunities. By grasping trends and avoiding pitfalls, you’re on the path to success. Visit Pass4itsure now for the latest resources and start your prep journey!